By 8x8 on Apr 16, 2020 11:15:34 PM
The stakes have never been higher for security and IT professionals
Concerns over COVID-19 related illness, government shelter in place orders, and inconsistent messaging between state and federal government as to when we might get back to our normal routines have left us guessing. The good news, despite these uncertain times, is that technology has enabled us to remain connected. However, with technology dependence comes risk. The use of virtual meetings technology has increased by more than 1000% in some cases. While this is great news for virtual meeting product companies, the hacker community at large has taken notice and is moving aggressively to exploit the new attack surface. The stakes have never been higher for security and IT professionals.
The FBI and other credible sources have reported four distinct virtual meeting product exploits that are noteworthy in my opinion. First, meeting hijacking occurs when someone enters a virtual meeting using compromised credentials to disrupt, usually with expletives or unsuitable content. Second, the takeover of a device camera or microphone for surreptitious recording. Third, unauthorised disclosure of your personal information to 3rd parties (like we don’t get enough junk email or telemarketer calls already) Fourth, communication intercept, may allow someone to exfiltrate data or communication from the meeting session.
Products should be built with privacy and security at their core
Now, what about the unknown exploits? I’m certain there are more to be found. At 8x8, the key to protecting our products doesn’t require a crystal ball or the ability to see the future. We need products that are designed with security and privacy in mind from the ground up. 8x8 Video Meetings, Powered by Jitsi, is a battle-hardened technology that has been built from the ground up with security, privacy, and compliance in mind. The product includes key features like strong encryption, randomised meeting names and password protection. The product continues to show its resilience even to the known exploits menacing other industry products today.
Another key layer of defence against current and unknown exploits is the platform in which the 8x8 products reside. 8x8’s single platform design was purposely built with security in mind providing unobstructed access to monitor, detect and respond to anomalous or suspect behaviour across 8x8’s technology stack. There is literally nothing in the way when security needs to engage and take action to protect our customers. The processes and controls protecting 8x8 Video Meetings are fully NIST 800-53 and ISO 27001 compliant. We rely on multiple accredited third party firms to assess our controls and processes then recommend enhancements that we roll into our continuous improvement process.
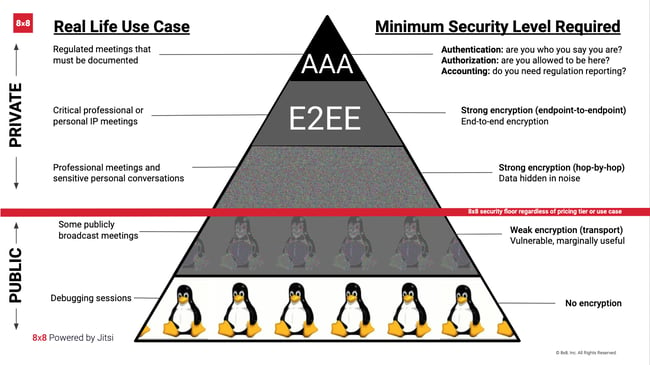
Encryption seems to be another key security element easily overlooked. Unfortunately, many products on the market still don’t use encryption or use a weak form of encryption as noted in the public section of the above graphic. In virtual meetings communication, a lack of strong encryption can lead to session data or even ID’s to be intercepted. 8x8 takes this seriously and has a non-negotiable position that all 8x8 Video Meetings will use strong-encryption, identified in the private section of the graphic.
The next major step is true end-to-end encryption
While strong encryption is a requirement from both my own and 8x8’s perspective, it’s still not enough. Video communications are subject to decrypt and re-crypt points across the communication channel. The Jitsi open-source developer community has published an RFC (request for comments) for true end-to-end encryption avoiding the need for any decrypt until the destination is reached. This is noted at the top right of the graphic. This advancement is a major step forward in making the 8x8 Video Meetings experience as secure as possible
One final thought for the Security and IT professionals reading this–which is, simply put, “Don't do it”. Don’t subject your organisation or yourself to unnecessary risk due to weak encryption or poorly designed virtual meetings products. The hacking community has found a new attack service in virtual meetings. Take the necessary steps to verify product encryption levels and make sure the products you're evaluating are built with security and privacy from the ground up. With all that’s at risk today, it’s not worth trusting your organisations data to any company that retrofits security and privacy. I’m proud of the work that 8x8’s doing to lead the way here and encourage you to contact us if you’re ready to learn more.

