By Sonia McPherson on Aug 21, 2018 2:06:48 PM
Cybercrime is a blight on the modern world, but you may be surprised to discover that it’s nothing new.
In fact, ever since people first invented communications technology there have been those who have found ways to ‘hack’ them.
Year: 1903
Type of attack: First recorded instance
Who: Guglielmo Marconi
What happened: The world’s first recorded incident of hacking took place when inventor and magician Nevil Maskelyne managed to disrupt Marconi’s demonstration of his supposedly secure wireless telegraphy technology.
Impact: Nevil managed to send rude messages via Morse code through the auditorium's projector and humiliate Marconi.
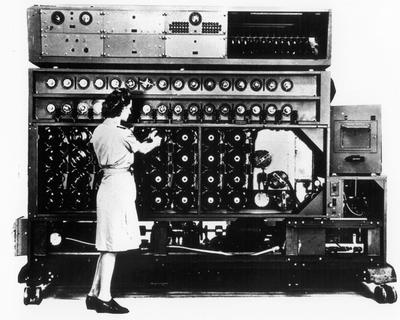
Year: 1939 – 1945
Who: – Bletchley Park vs Nazi Germany
What happened: Thanks to the code breakers at Bletchley Park, the Allies were able to read the enemies intelligence reports and orders. The code breakers played a key role in the defeat of Nazi Germany.
Impact: With the capture of a German Enigma machine the tide of World War Two swung to the Allies.
Year: 1957
Type of attack: Phreaking
Who: – Joe Engressia
What happened: A technique known as Phreaking was discovered by a blind seven-year-old boy. The boy was able to whistle at the exact same frequency as that used by telephone lines.
Impacts: Hackers quickly exploited the discovery and used the technique to get free long-distance international phone calls.
Year: 1963
What happened: The first ever reference to malicious hackers is published by MIT’s student newspaper.
Year: 1980
Who: New York Times
What happened: The New York Times Describe Hackers as:
‘Technical experts; skilled, often young, computer programmers, who almost whimsically probe the defences of a computer system, searching out the limits and the possibilities of the machine. Despite their seemingly subversive role, hackers are a recognized asset in the computer industry, often highly prized.’

Year: 1982
Type of attack: Logic Bomb
Who: USA vs Soviet Union
What happened: The CIA supposedly blew up a Soviet pipeline in Siberia
Impacts: The CIA created what is now known as a Logic Bomb and used it against a Soviet pipeline. The ‘bomb’ caused the pipelines controls to go haywire resulting in an explosion that was reportedly seen from space.
Year: 1983
Who: Hollywood
What happened: With the Cold War still in progress, Hollywood released the movie War Games creating hysteria over hacking. The movie depicts hackers breaching US systems and launching nuclear missiles.
Impacts: Public awareness of hackers increased but they had the pants scared off of them. Setting a precedent for the negative public image of hackers for years to come.
Year: 1984
Type of attack: Password breach
Who: BT Prestel data service
What happened: Using home computers, Robert Schifreen and Stephen Gold gained access to BT’s Prestel interactive view data service. Schifreen gained access by observing a Prestel engineer inputting a username of 22222222 and a password of 1234. Using this information Schifreen and Gold explored the BT network and even gained access to Prince Philips personal message inbox.
Impacts: Breach of BT’s data service and reputational damage
Year: 1984
Type of attack: Trojan/ Ransomware
Who: Dr. Joseph Popp
What happened: Dr Popp introduced the AIDS Trojan Horse. AIDS would count the number of times a computer was booted. Once the boot count reached 90, AIDS would then hide directories and encrypt the names of all the files on drive C.
Impacts: The Trojan effectively rendered a system unusable. The user would then be asked renew the computer’s license' and contact PC Cyborg Corporation for payment. This involved sending $189 to a post office located in Panama. Dr. Joseph Popp was arrested for introducing the Trojan, but was declared mentally unfit to stand trial.
Year: 1986
Who: US Government
What happened: As computers became popular, the number of government and corporate systems being hacked increased sharply prompting the US government to introduce the Computer Fraud and Abuse Act. Other nations soon followed. In the UK, the first conviction for illegally accessing a computer system was made.
Year: 1988
Who: Suspected Russian Hackers vs USA
What happened: Hackers breached sensitive US computer systems. Dubbed Moonlight Maze, the attack reportedly breached the Pentagon, Nasa and other sensitive areas. The attack was discovered in 1988 but had been ongoing for 2 years.
Year: 1988
Who: Robert Morris
Type of attack: Malware - Worm
What happened: Morris, a graduate student at Cornell University creates a worm that infects the US governments ARPA network (the precursor to the internet).
Impact: The worm infects 6,000 computers and resulted in Morris being fined $10,000. In the same year the First National Bank falls victim to data theft worth $70 million.
Year: 1990
Who: British Government
What happened: The UK government introduces the Computer Misuse Act that criminalises any unauthorised access to computer systems.
Year: 1994
Who: Citibank
Type of attack: Phishing
What happened: Russian hacker Vladimir Levin managed to siphon $10 million from Citibank and transfer it to bank accounts located all over the world.
Impact: All but $400,000 of the stolen money is recovered by the authorities.
Year: 1999
Type of attack: Phishing/ Malware
Who: David L. Smith - Melissa Virus
What happened: The virus was spread via emails, that when opened disabled safeguards in Word 97 and Word 2000 programmes. If the victim was a user of the Microsoft Outlook e-mail programme the virus would resend itself to the first 50 people in the user’s address books.
Impact: The virus is thought to have infected 20% of the computers available at the time. Microsoft was forced to close down all incoming e-mails. The virus cost millions of dollars in damages and Smith was arrested and sent to prison for 10 years. He served just 10 months and was fined $5,000.
Year: 2000
Type of attack: DDOS
Who: Amazon, Dell, CNN, eBay
What happened: A 15-year old Canadian hacker calling himself Mafia Boy launched the first documented DOS attacks against several major commerce websites.
Impact: (FBI) estimated that the affected sites suffered $1.7 billion in damages
Year:2000
Type of attack: Phishing/Malware- Worm
Who: Windows PCs
What happened: A worm attacked tens of millions of Windows PCs by being spread via an email message with the subject line "ILOVEYOU”. The worm originated in the Philippines before spreading worldwide.
Impact: The outbreak was later estimated to have caused $5.5–8.7 billion in damages worldwide, and estimated to cost $15 billion to remove the worm.
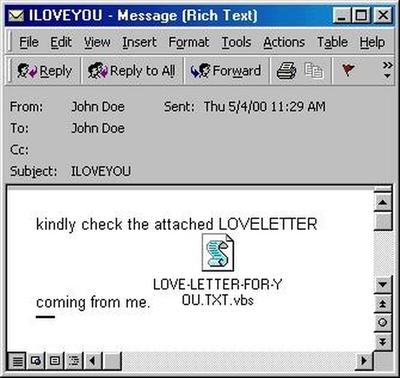
Year: 2001
Type of attack: Phishing/Malware – Worm
Who: Jan de Wit/ Anna Kournikova
What happened: A 20-year old Dutch student created a Worm hidden in an email attachment featuring tennis star Anna Kournikova. Once triggered the worm would forward itself to every contact in the victims Microsoft Outlook address book.
Impact: The worm infected thousands of computers worldwide but did not damage them, it did however, overwhelm some companies' computer systems with the huge volume of e-mails it created.
Year: 2001
Type of attack: Malware – Virus
What: Klez Virus
What happened: The Klez virus is regarded as one of the most destructive viruses in history. In its original form it wasn’t particularly harmful but over time hackers adapted it to their purposes and made it marginally more dangerous. Infamous for being able to spoof email addresses as well as having the ability to infect a receiver’s computer without them downloading or executing a malicious attachment.
Impact: Klez and its variants are reported to have inflicted $19.8 billion in damage worldwide.
Year: 2007
Type of attack: Man-in-the-Middle
What: TJX
What happened: Regarded as one of the biggest hacks in history, TJX was breached by hackers gaining access through a poorly secured wireless LAN. The hackers remained undetected in TJXs payment system for 18 months.
Impact: The card details of at least 45 million customers were stolen and cost TJX billions in remediation costs, fines and law suits. Reputational damage was also severe.

Year: 2010
Type of attack: Stuxnet Worm
Who: USA/Israel vs Iran
What happened: The Stuxnet worm was used to severely damage Iran’s nuclear programme. Stuxnet is the first Malware to be able to spy on and disrupt industrial systems.
Impact: Aside from damaging Iran’s nuclear programme the worm spread far and wide but was relatively harmless to computers and networks that did not meet specific requirements. Stuxnet is considered to be the worlds first targeted cyber weapon.
Year: 2011
Type of attack: DDoS/ Intrusion
Who: Sony Playstation Network
What happened: The hacktivist group Anonymous launched a DDoS attack against the Playstation network. This attack was followed by an intrusion that resulted in millions of customer details being stolen.
Impact: 77 million accounts were affected. The fallout cost Sony millions in damages and bad publicity.
Year: 2013
Type of attack: Spear Phishing/ Intrusion via 3rd party/ malware
Who: Target
What happened: Hackers breached Targets by stealing credentials from a 3rd party heating company which had access to Targets networks to monitor their systems. The company fell victim to a spear phishing attack a few months before the main attack on Target. The hackers then installed malware onto Targets point of sell systems that stole customer credit card details and sent them to a compromised Target server. The data was then sent overseas.
Impact: 1-3 million card details were stolen. The breach cost Target hundreds of millions of Dollars.
Year: 2014
Type of attack: Phishing
Who: JP Morgan Chase
What happened: Hackers gained entry to JP Morgans systems after an employee fell to a phishing attack that compromised their user credentials. The hackers stole the details of 83 million of the banks customers.
Impact: The reputational damage was high and JP Morgan pledged to double its cybersecurity spending to £311 million as a result of the breach.
Year: 2014
Type of attack: Malware
Who: Sony Pictures
What happened: Suspected North Korean hackers leaked confidential data as a response to the release of the film ‘The Interview’, a comedy about the assassination of North Korean dictator Jim Jong-un.
Impact: The hack cost Sony millions of Dollars as well as reputationally.
Year: 2015
Type of attack: Hacktivism
Who: Ashley Maddison
What happened: Hackers leaked the personal details of users of the notorious dating site Ashley Maddison. The hacked information was used to blackmail high profile users and expose their infidelity.
Impact: Aside from a few divorces and payments to blackmailers the biggest cost was to Ashley Maddison’s already dubious reputation and the reputations of those exposed.
Year: 2015
Type of attack: unpatched software exploit
Who: Carphone Warehouse
What happened: A number of security failures resulted in hackers compromising the details of 3 million customers. It was shown that the company was running unpatched software, had no antivirus on servers and up to 30-40 members of staff shared the same password and login details.
Impact: The Information Commissioners Office (ICO) fined Carphone Warehouse £400,000
Year: 2015
Type of attack: SQL injection
Who: TalkTalk
What happened: A 15-year old boy hacked TalkTalk leaking 157,000 of its customers details.
Impact: Aside from massive reputational damage the breach has cost millions in lost customers, fines and the introduction of new cybersecurity measures.
Year: 2016
Type of attack: DDoS/ Botnet
Who: Dyn
What happened: A massive DDoS attack against the Domain Name System operated by Dyn caused major outages and disruption to major internet platforms across the USA and Europe. The attack is thought to have been strengthened by IoT devices compromised by the Mirai Botnet.
Impact: Over 100,000 IoT devices were used in the attack which is one of the largest DDoS attacks in history.
Year: 2016
Type of attack: Data breach
Who: Yahoo
What happened: A billion user details were stolen making it one of the biggest hacks ever.
Impact: At the time Yahoo was negotiating its sale to Verizon who apparently slashed its offer by $1 billion as a consequence.
Year: 2017
Type of attack: Breach through unpatched software
Who: Equifax
What happened: US credit reporting company Equifax was breached via a web- application vulnerability that resulted in the theft of the details of 143 million people. A patch was available for the exploited vulnerability.
Impact: One of the largest data thefts in history the attack is likely to have cost Equifax up to $90million and its reputation severely tarnished.
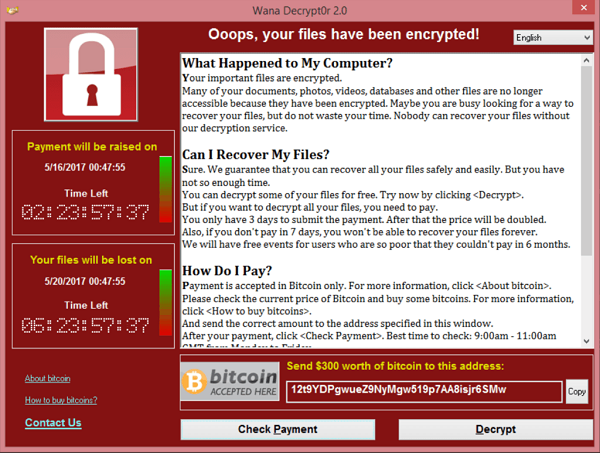
Year: 2017
Type of attack: Ransomware
What: WannaCry
What happened: Over 200,000 computers were infected across 150 countries. One of the biggest victims was the National Health Service which was forced to cancel operations as a result. According to Europol the size of the ransomware campaign was unprecedented in its scale.
Impact: Estimates of the damage caused as a result range from as high as $4 billion to the hundreds of thousands.
Year: 2017
Type of attack: Ransomware
What: NotPetya
What happened: Several nations were impacted, but the majority of cases occurred in Ukraine and Russia.
Impact: The British government and others officially blamed the outbreak on Russia. The ransomware knocked out at least 10% of Ukraine’s computers and was thought to be an attack as a result of the conflict in the country. The disruption caused over $1 billion in damages.

Year: 2017
Type of attack: Exploited vulnerability
Who: Equifax
What happened: The breach exposed the sensitive data of over 143 million people. Half the population of the USA.
Impact: The breach is one of the most costly in history and has cost the company more than $439 million.

Year:2018
Type of attack: Hardware vulnerabilities
What: Meltdown and Spectre
What happened: The discovered hardware vulnerabilities in devices using Intel, AMD and ARM chips, allow programs to steal data which is currently processed on a computer. While programs are typically not permitted to read data from other programs, a malicious program can exploit Meltdown and Spectre to get hold of secrets stored in the memory of other running programs.
Impact: The revelation that virtually all devices suffer from the vulnerability caused panic. Intel and others released patches that had the negative effect of slowing down devices, and other exploits have already been discovered.
Year: 2018
Type of attack: Malware
Who: Multiple websites
What happened: Crypto mining
Impact: Several websites including the UK’s ICO website were temporarily taken offline after it was discovered that a piece of malware was hijacking site visitor processing power in order to mine a cryptocurrency. It brought the issue of crypto mining into the mainstream.
Year: 2018
Type of attack: Malware
Who: Pyeongchang Winter Olympics
What happened: The official website of the 2018 Pyeongchang Winter Olympic Games was knocked offline by malware.
Impact: Major sporting events are often targeted hackers. The events main website was taken offline for 12 hours impacting on ticket sales and distribution.
For more information on how we can protect you against the above attacks email; discover@everycloud.co.uk, www.everycloud.co.uk, Tel: 0203 904 3185
Source; https://www.xqcyber.com/cyberscore/show/a-history-of-hacking
